It seems that every other week there is a news story about some company’s servers being hacked, exposing our personal information. The most egregious hacks are well publicized, like last year’s Equifax breach that exposed the personal information of virtually every American with a credit history. But our Social Security numbers are not the only thing hackers are after. We have lots of valuable information on the internet. From your Apple account to your credit cards, follow along to learn more about the secret world of hackers looking to exploit your accounts.
Table of Contents
ToggleHow breaches happen
Since the advent of the internet, computers around the world become more and more intertwined through a growing, powerful network. This means every computer from our personal laptop and desktop computers at home to major data processing mega computers run by banks and credit card companies is part of the growing network of the internet. This is a good thing because it gives consumers and businesses near-instant access to information. It enables services like Google, Netflix, Amazon, and Facebook. Our smartphones wouldn’t be very smart without a connection to the internet.
But if we can connect to the internet, so can bad guys around the world who want to use that data for malicious purposes. This includes groups like the hackers who broke into Target, Home Depot, and other retailer databases to steal payment information to sketchy data miners like Cambridge Analytics who hijacked Facebook user information to promote a political campaign.
Breaches usually don’t happen because of one or two little mistakes. They are generally the result of a confluence of events. That includes lax security practices at the “victim” and a targeted hacking effort by a malicious individual or group.
The worst information to lose is already public
Last year, Equifax was hacked in the most egregious example of a data breach in American history. The fallout is unprecedented, with credit data for 145 million Americans leaked in a failure of Equifax to maintain advised security standards. That hack included names, addresses, phone numbers, and social security numbers for virtually every American adult who has had a credit card or any other type of loan in the last ten years.
But that doesn’t mean hackers are going to stop. They attack banks, governments, and other institutions regularly with an end goal of financial gain. In many cases, the computer hackers won’t exploit the data they find themselves. Instead, they will sell it to the highest bidder and accept payment in Bitcoin and other cryptocurrencies, making the transaction untraceable.
Data thieves don’t stop at social security numbers and other financial information, they target accounts like Netflix, Apple, and Google as well, according to a study by Top10VPN, a VPN review site. They went undercover in the “dark web” and found out what each account is worth.
What your accounts are worth online
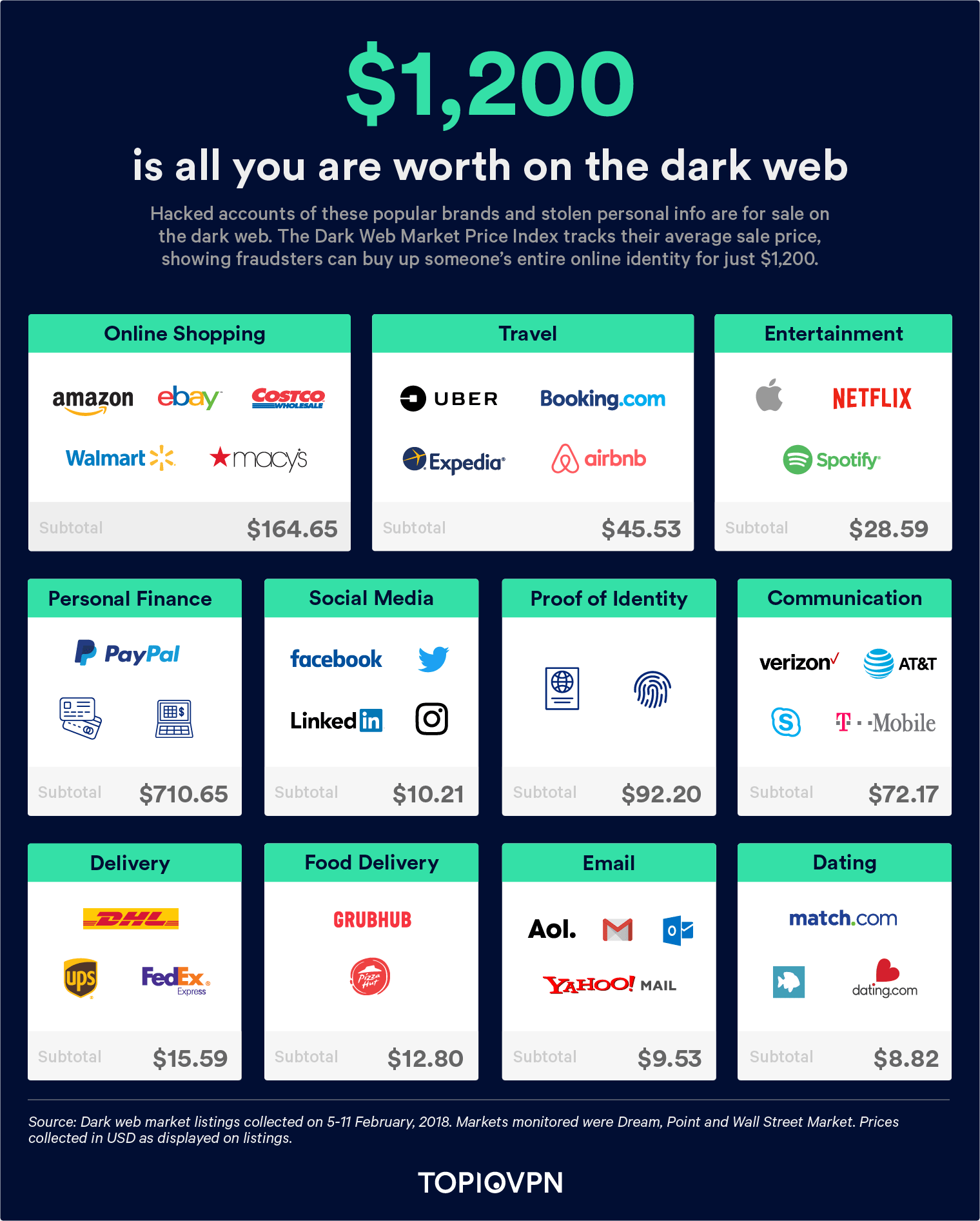
Not surprising, shopping accounts are among the most expensive in the online black market. Accounts from eBay, Amazon, Costco, Walmart, and Macy’s give criminals access to a wide range of products and overnight shipping, all at your expense, before you or the credit card company identify the fraud. These accounts are worth anywhere from $2 each to $15 each.
The most valuable are financial accounts like PayPal, which can value in range from $35 for credit reports up to $247 for PayPal logins. With these logins, a thief can make withdrawals from your bank account, go shopping on your credit cards, and do a ton of damage before detection. I’m not sure why anyone would want a stolen Spotify or Plenty of Fish login, as those services are free, but even those are worth a little something to the right buyer.
Use strong password security to protect yourself
To avoid falling victim, you should use strong, unique passwords on every site. Using a password generator and a password wallet like LastPass or Dashlane, you can easily handle what would otherwise be a monumental task. You can use LastPass, for example, to generate a password when you sign up for a new site. You’ll save it to LastPass, and it will auto-fill the next time you visit the site’s login page.
With that in mind, you should have no problem using a unique, long password. With LastPass installed, you can setup password guidelines. You can use a 20 character, random string with letters, numbers, and symbols that is different on every site. If one site gets hacked, they won’t have access to all of your sites because none share the same password.
Also, use two-factor authentication where supported. This gives your accounts an extra layer of security. It relies on your phone being there physically during the login process, which should only happen when you are present.
Bad guys are out there but you don’t have to be a victim
Cybercriminals are a matter of fact, and hail from all corners of the Earth. From here in the United States to China, armies of hackers are hard at work trying to steal our data. With good password practices, you should still stay vigilant, but you have little to worry about.